



 Last Update: 17 Jul 2000
Last Update: 17 Jul 2000
16. Securing Windows Clients (3.11/95/98)
- Don't expect a high security from these systems, switch to NT or
UNIX, or buy 3rd party security produsts if sensitive data is handled by
DOS/Windows/Win95/Win98.
- Update your Win95 & WfW clients with the password security patch,
even better disable caching!
- Win95 Dialup networking: don't save passwords locally.
- Teach users to choose strong passwords, to change them regularly and
to lock screens or stop machines when not is use.
- Run viral scanners regularly and teach users
to use the scanner on all floppy disks. Ensure that clear organisation procedures are in
place to deal with a "viral outbreak".
- Don't store confidential information on the PC.
- If PCs access confidential servers, consider physically locking their
casings and attaching them to their desks.
- Don't use workgroups to share confidential data.
- Don't use workgroups to share high availability data.
- Scope: 3rd party connectivity products/protocols such as
Netware, DECnet, Vines or NFS are not covered here.
- Windows '95 is just a shinier version of Windows for workgroups. It
is based on (primitive) 16-bit DOS and should not be relied up for much security. Although
Windows 95 offers more security than it's predecessors, these security features should not
be regarded as an effective barrier to the knowledgeable hacker.
- Win98 is almost identical to Win95, it just has a few new feature,
different GUI and support for new hardware such as USB.
- No data is to be kept on PC workstations.
- Use an disk controller which encrypts data on the fly. Normally the
controller asks for a password during PC boot.
The use of laptops is to be minimised, as they represent a serious
security risk - even if the trend is more and more towards mobile computing. They allow
uncontrolled exchange of large amounts of data.
- Use an EPROM boot password (although it offers little protection).
- When transporting a Laptop via public transport, carry as hand
baggage.
- An anti-virus program must be installed.
- Data should be encrypted with a suitable software (see the Tools
section at the end of this chapter).
See the Windows 95 Resource kit and the WfW 3.11 Resource kit.
These operating systems cannot be certified to ITSEC or TCSEC
standards. See the Operating System overview section.
Viruses are programs that self replicate: they attempt to spread
from computer to computer and may cause damage (by erasing or corrupting data) or
may annoy users (changing screen contents, printing messages). Viruses are a
mostly PC (and more recently Macintosh) phenomenon. To combat viruses, the following
measures are to be taken:
- Educate users: if they understand what viruses do, how they are
propagated, users will be more careful.
- A Standard virus detection tool should be
installed on all PCs. The virus signature list should be updated every few days|weeks|months,
depending on system sensitivity.
- The scanner should detect macro viruses and stay resident in memory,
watch all file operations.
- If a virus is found, notify the Helpdesk/support personnel
immediately. The workstation should be disconnected from the network.
- Consider membership of an organisation such as the ICSA www.icsa.com or CERT to keep abreast of Virus/security
issues and to have help available in case of a major virus threat.
In addition:
- Install applications on servers and mount them read-only from
workstations.
- Install applications on a test machine, check for viruses, then
install on servers.
- Do regular system backups of servers. Keep backups for up to a year.
- Restrict user access to floppy drives (but email & the web still
provides a way of downloading dangerous software.
- See also the MS-Office
section for tips regarding Word/Excel.
Hoax virus protection:
The many "hoax" viruses (false warnings, jokes) may waste
much of support personnel's time. It's difficult to protect against them, but the
following may help:
Recommended for sensitive hosts: Windows 95 can be configured so
that a user must log into an NT domain (i.e. the user cannot log in locally) with
the Profile Editor (see Access Control section).
A secure Audit trail is almost impossible on a non DAC system.
DOS
- Mark autoexec.bat, config.sys and important .ini files as read-only
(using attrib -r). (This may cause administration hassle though...)
- Remove intersrv.exe and interlnk.exe to prevent the use of serial
communications.
Windows for Workgroups
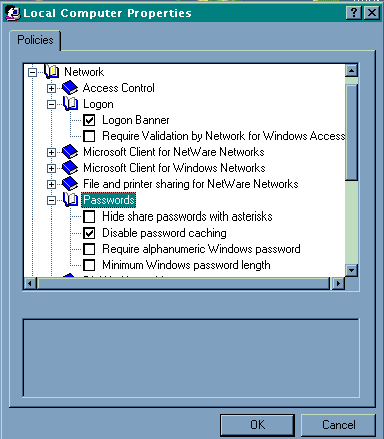
- Using admincfg.exe, Configure wfwsys.cfg on
each workstation. File, Printer and DDE sharing should be disabled. In the "Security
Settings" , password caching should be disabled, "require validated logon to
NT" should be enabled. "Update security configuration from server" and
protect the config file with a password (perhaps one password for each domain).
 The logon banner should
also be used to warn the user that he is connecting to sensitive data.
The logon banner should
also be used to warn the user that he is connecting to sensitive data. Remove unneeded icons
from the user desktop (Network install, windows setup, telnet, ftp...)
Remove unneeded icons
from the user desktop (Network install, windows setup, telnet, ftp...)  Restrict program manager
functionality. e.g. No file menu, no "run" option, no personalisation. (see
progman.ini entries: NoSaveSettings, NoRun, NoClose, NoFileMenu, Editlevel)
Restrict program manager
functionality. e.g. No file menu, no "run" option, no personalisation. (see
progman.ini entries: NoSaveSettings, NoRun, NoClose, NoFileMenu, Editlevel)
Win95
 Set up a system policy via
the policy editor (install poledit.exe in admin\Apptools on the Win95 CD). The policy
editor should not be installed on user workstations. There are three different types of
profiles:
Set up a system policy via
the policy editor (install poledit.exe in admin\Apptools on the Win95 CD). The policy
editor should not be installed on user workstations. There are three different types of
profiles:
- A user profile consists of user-specific information contained
in the file USER.DAT, one of the two files in the Windows 95 Registry. User profiles need
to be enabled (see control panel -> passwords) only for the computers where they will
be used.
* Multiple users on a computer can retain their personal settings.
* "Roving" users can log on to the network from any computer and work with the
same desktop settings (if the profiles are stored in NETLOGON).
* Windows 95 automatically maintains each user's profile.
- Mandatory profiles can be used to enforce consistent desktops.
This is useful for novice users, for reducing training costs and support costs.
- System policies allow you to override local Registry values
for user or computer settings. Policies are defined in a policy (.POL) file, usually
called config.pol. When a user logs on, system policy settings overwrite default settings
in the Registry. You can also set system policies to contain additional custom settings
specific to the network.
Unlike SYSTEM.DAT and USER.DAT (the two files that make up the Registry), CONFIG.POL is
not a required component of Windows 95 Setup and, when implemented, is stored on the logon
server, not the local computer.
System policies can be used to enforce system configuration (what users are allowed to do
from the desktop, what they are allowed to configure using Control Panel, centrally
configure network settings and to customise certain parts of the desktop, such as Network
Neighbourhood or the Programs folder.
To set up automatic downloading of the policy from a Windows NT server on login:
1 On the File menu, click Open Registry.
2 Double-click Local Computer.
3 Click the plus sign beside Network.
4 Click the plus sign beside Microsoft Client For Windows Networks, and then click Log On
To Windows NT.
5 Type the Windows NT domain name.
6 On the primary domain controller, create a folder named NETLOGON, and then share it.
7 Save the policy file in this folder. Make sure the policy file has a .pol extension.
TBD:- what should be defined in config.pol for each security level, per user &
computer (e.g. logon banner, force logon to NT domain, disable file/printer sharing,
disable registry editors, disable password caching, disable dial-in networking, desktop
settings...)? Can the user delete/change his config.pol (NETLOGON permissions? This must
be prevented).
Discretionary access control is not possible, mainly due to the FAT
filesystem.
 Lock the PC housing
where possible.
Lock the PC housing
where possible.
 Use boot passwords. If possible use separate
user and administrator passwords.
Use boot passwords. If possible use separate
user and administrator passwords.
 For secure(ish) Win95 startup, disable the
functions keys F5,F6 and F8 by setting Bootkeys=0 in msdos.sys. This will make debugging
of startup problems more difficult, however.
For secure(ish) Win95 startup, disable the
functions keys F5,F6 and F8 by setting Bootkeys=0 in msdos.sys. This will make debugging
of startup problems more difficult, however.
 A special utility should
be installed on all PCs to erase files completely (e.g. F-Secure Desktop, see
below).
A special utility should
be installed on all PCs to erase files completely (e.g. F-Secure Desktop, see
below).
Workgroups: WfW 3.11 supports share-level security, but not
user-level security.
 AVOID using Workgroups,
use Domains (Lan-Manager, NT) or NFS instead.
AVOID using Workgroups,
use Domains (Lan-Manager, NT) or NFS instead.
 Disable Workgroups
Disable Workgroups
 Do not use as a RAS
server.
Do not use as a RAS
server.
 PC clients should not be used as ftp or http
servers.
PC clients should not be used as ftp or http
servers.
 Disable floppy boot in BIOS setup.
Disable floppy boot in BIOS setup.
not supported.
Install a minimum of network protocols. If possible do not install
NetBEUI on subnetted networks - use TCP/IP & WINS servers instead.
PCs should not be used for routing. A default gateway should
be defined (Control Panel->Networks-> TCP/IP) and all TCP/IP packets for machines
outside the current subnet will be forwarded to this gateway. Normally the default
gateway is the router.
- Registry Backups:
 The
registry should be an integral part of tape backups.
The
registry should be an integral part of tape backups.

 Repair diskette: keep in a locked, fireproof safe. Also copy
system.dat, config.sys, autoexec.dat, win.ini and system.ini to a subdirectory on the
repair diskette.
Repair diskette: keep in a locked, fireproof safe. Also copy
system.dat, config.sys, autoexec.dat, win.ini and system.ini to a subdirectory on the
repair diskette.- Recovery:
- Every time WIn95 successfully boots, it creates a backup of the
registry files with a .da0 extension. If the .dat seems corrupt on startup, WIn95 uses the
backup .dao.
- When booted in safe mode, the registry is not backed up, it
assumes thay are damaged. If you have manual backups of the registry, they can be restored
in safe mode.
- The system.1st in the root directory is a copy of the first
registry at setup time. A damaged registry can be restored by changing the attributes and
copying this file to system.dat. Also if a machine is hanging on startup, use F8 to select
logging and continue booting When it blocks, boot with a floppy disk and examine bootlog.txt
to see what device/driver is causing the problem.
Quotas etc. are not supported, but are not really necessary on
client machines.
- Install PCs from the network. The advantages are:
1. The OS is installed from a secure master copy with the latest patches.
2. The OS is preconfigured according to your needs.
3. Standard applications are automatically installed.
4. Much faster.
The disadvantage is that it is very sifficult to setup, especially when many different
types of hardware are used.
- SMS offers a disciplined change control system for (50 or more)
Windows clients.
- Windows for Workgroups has serious security bugs!
- Win95 has serious security bugs, some can be fixed by downloading the
fixes from www.microsoft.com/windows/download/
. But the fixes are frequent and need to be tested.
- Consider moving sensitive clients to NT.
- Some (old) example of patches and updates are:
| Date |
Problem |
Fix archive |
| 13.12.95 |
The password cache has weak encryption (exposes all server systems
used by a Win95 client). |
mspwlupd.exe |
| 20.10.95 |
Problem with NetWare file sharing (read access to local files) |
nwsrvupd.exe |
| 20.10.95 |
Problem with Microsoft networks file sharing (can read entire
disk). |
vservupd.exe |
| 6.12.95 |
OLE can hide parts of deleted files in Office 95 files (i.e.
Winword, Excel, PowerPoint). These parts are visible via a plain-text editor, for example,
notepad. |
ole32upd.exe |
The above patches are available as a "Service Pack 1" for
Win 95.
May'96 update: A new batch of updates need to be installed over Service Pack 1 to
fix new bugs. See:
File name size
krnlupd.exe 296,960
mspwlupd2.exe 284,160
krnltoys.exe 54,586
oleupd.exe 404,992
cover_pg.exe 147,456
inetmail.exe 241,152
dlc32upd.exe 180,224
The Win95 Briefcase utility is useful for synchronising Laptops and
servers. However, be aware that if the filesystem on the server is a compressed NTFS
directory, the briefcase will only be "partially" synchronised. I prefer using NT's "robocopy" for synchronisation.
HW RAID is a possibility, but it is better to simply store data on a
server.
WfW 3.11 has a utility called admincfg.exe which may be
used to configure several network security options.
PGP is a great all round security tool, with File, Disk and Email
encryption. (See chapter 7) www.pgp.com and www.pgpi.com for International users..
For email, see also S/MIME.
- PGP is always work checking out.
- F-Secure Desktop: This product,
exported from Datafellows in Finland, allows military strength encryption of files on
Windows systems with an easy-to-use GUI. Recomended. See the analysis in the mechanisms chapter.
- Ironware from AEC Ltd. in the Czech Republic (www.aec-security.com) offers secure file deletion,
strong file encryption with compression, secure file transfer, file signing with SHA,
email encryption and FTP encryption. Price ~$140.
- Secrets is a Winows based file encryption program with group
keys and data recovery. www.sapher.co.uk
- CyberAngel by Sentry Software ( www.sentryinc.com ) offers file encryption, from DES
to 448bit blowfish.
- Latches from Rhea international, U.K. ( www.rheagroup.com ) offers secure logon, audit logs,
silent alarms, file encryption DAC& MAC, boot protection, role based access control
and supports physical access tokens.
- Destroy: This free utility allows
files to be securely deleted under DOS:
DESTROY - A file deletion and security utility for MSDOS. When
you use "del" to delete a file, it can often be recovered by use of
"undelete" or other tools. DESTROY is different. It wipes the file before
deleting it. It also destroys the directory entry. Recovery tools will only recover a
small file full of zeros.
- StopLight: StopLight for DOS, Windows and
Win95 controls access to files, drives, directories with Read/Write/Create/delete/Execute
privileges, by providing security at the OS level. Even if a computer is booted with a DOS
diskette it is protected. Full disk encryption (real time encryption is an option) for
laptops, in addition to optional boot sector encryption. Logging and auditing are included
too. Most network types are supported. See also www.safe.net
- Stoplock V
- Raxco EAC, SECUREcard
No PC should be without a virus protection.
Virus tools tend to have three functions:
1. Generic monitoring (prevention)
2. Scanning (looking for viral signatures)
3. Integrity checkers (looking for changes files)
There are literally hundreds of anti-virus programs available. Typically an enterprise
buys a site wide license for all machines with regular (e.g. monthly) automatic updates.
If you're shopping for a new anti-virus:
- make sure that it works with DOS, NT, Win95 and conventional Windows
(each have special requirements).
- It should also protect against macro viruses (i.e. viruses in
MS-Office documents or other desktop applications which may contains macros) and possible
ActiveX viruses..
- It's user interface should be friendly and easy to use (minimum user
education necessary).
- It should also be possible to upgrade the anti-virus from a server
quickly, regularly and easily.
- Some examples of current products (there are many, many products on
the market): McAfee, Norton Anti-virus (maybe expensive for large sites), IBM AV
(Anti-Virus), TBAV (Thunderbyte Anti-Virus from ESaSS B.V), Norman (www.normanuk.com), VirusNet (Safetynet Inc.) and also
the DataFellows product.
- See also the list of products certified to Secure Computing Magazines
"checkmark" standard at www.westcoast.com/checkmark
.




 Last Update: 17 Jul 2000
Last Update: 17 Jul 2000
![]() Lock the PC housing
where possible.
Lock the PC housing
where possible.![]() Use boot passwords. If possible use separate
user and administrator passwords.
Use boot passwords. If possible use separate
user and administrator passwords.![]() For secure(ish) Win95 startup, disable the
functions keys F5,F6 and F8 by setting Bootkeys=0 in msdos.sys. This will make debugging
of startup problems more difficult, however.
For secure(ish) Win95 startup, disable the
functions keys F5,F6 and F8 by setting Bootkeys=0 in msdos.sys. This will make debugging
of startup problems more difficult, however. ![]() A special utility should
be installed on all PCs to erase files completely (e.g. F-Secure Desktop, see
below).
A special utility should
be installed on all PCs to erase files completely (e.g. F-Secure Desktop, see
below). ![]() AVOID using Workgroups,
use Domains (Lan-Manager, NT) or NFS instead.
AVOID using Workgroups,
use Domains (Lan-Manager, NT) or NFS instead.![]() Disable Workgroups
Disable Workgroups ![]() Do not use as a RAS
server.
Do not use as a RAS
server.![]() PC clients should not be used as ftp or http
servers.
PC clients should not be used as ftp or http
servers.![]() Disable floppy boot in BIOS setup.
Disable floppy boot in BIOS setup.